How To Lock Down WordPress – WordPress Security Guide 2022
The Internet live stats show that more than 100,000 websites are hacked every day, making the hardening of your WordPress website a priority call.
The information provided below on the WordPress hardening my change as new vulnerabilities emerge.
Secure WordPress Hosting
Web server security for which your WordPress host is responsible for is paramount. Choose a host that you can trust with your business. Alternatively, you can host on your own VPS but you need to have the necessary technical knowledge to do all security matters and system configurations by yourself.
Server hardening: Key to maintaining a thoroughly secure WordPress environment. It takes multiple layers of hardware and software level security measures to ensure the IT infrastructure hosting WordPress sites is capable of defending against sophisticated threats, both physical and virtual. Ensure the server operating systems and other security software are well tested and scanned for vulnerabilities and malware.
Server-level firewalls and intrusion detection systems should be in place before installing WordPress on the server to keep it well-protected even during the WordPress installation and website construction phases. However, every software installed on the machine intended to protect WordPress content should be compatible with the latest database management systems to maintain optimal performance. The server should also be configured to use secure networking and file transfer encryption protocols (such as SFTP instead of FTP) to hide away sensitive content from malicious intruders.
Use Latest PHP Version
PHP is the backbone of your WordPress site and so using the latest version on your server is very important. Each major release of PHP is typically fully supported for two years after its release. During that time, bugs and security issues are fixed and patch on a regular basis. Anyone running on version PHP 7.1 or below no longer has security support and are exposed to unpatched security vulnerabilities.
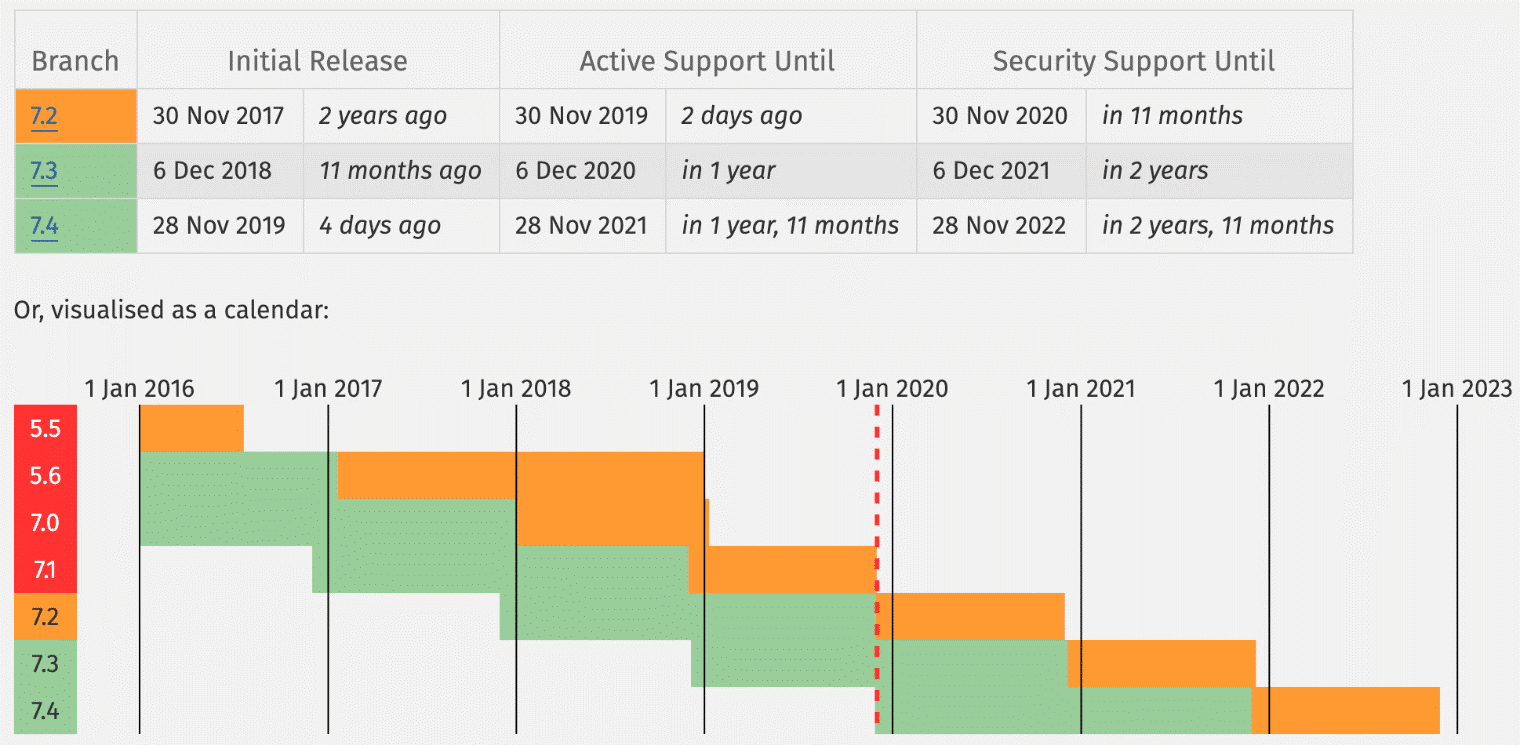
Note: Visit the WordPress Stats page and view the percentile usage of the common sorts of systems users are running WordPress on. This is a security and performance concern to their websites.
Use Clever and Secure Usernames and Passwords
One of the best and simplest ways to harden WordPress security is simply to use clever usernames and passwords.
Note: Surprisingly, users use poor choice of passwords including (ensure that you never use any of the following):
- 123456
- password
- 123456789
- 12345678
- 12345
- 111111
- 1234567
- sunshine
- qwerty
- iloveyou
If you don’t know how to create a secure password, allow the system to generate one for you during the installation process of WordPress. Some of the best security starts from the basics. Google has some great recommendations on how to choose a strong password. Or you can use an online tool like Strong Password Generator. It is also important to use different passwords for every website. The best way to store them is locally in an encrypted database on your computer.
And as far as your WordPress install goes you should never use the default “admin” username. Create a unique WordPress username for the administrator account and delete the “admin” user if it exists. You can do this by adding a new user under “Users” in the dashboard and assigning it the “Administrator” profile.
You can also rename your current admin username manually in phpMyAdmin with the following command. As always, a precautionary measure to ensure that you make sure to back up your database before editing tables.
UPDATE wp_users SET user_login = 'newcomplexadminuser' WHERE user_login = 'admin';
Latest Versions of WordPress, Plugins, and Themes
Another very important way to harden your WordPress security is to always keep it up to date. This includes WordPress core, plugins, and themes. These are updated for enhancements and bug fixes.
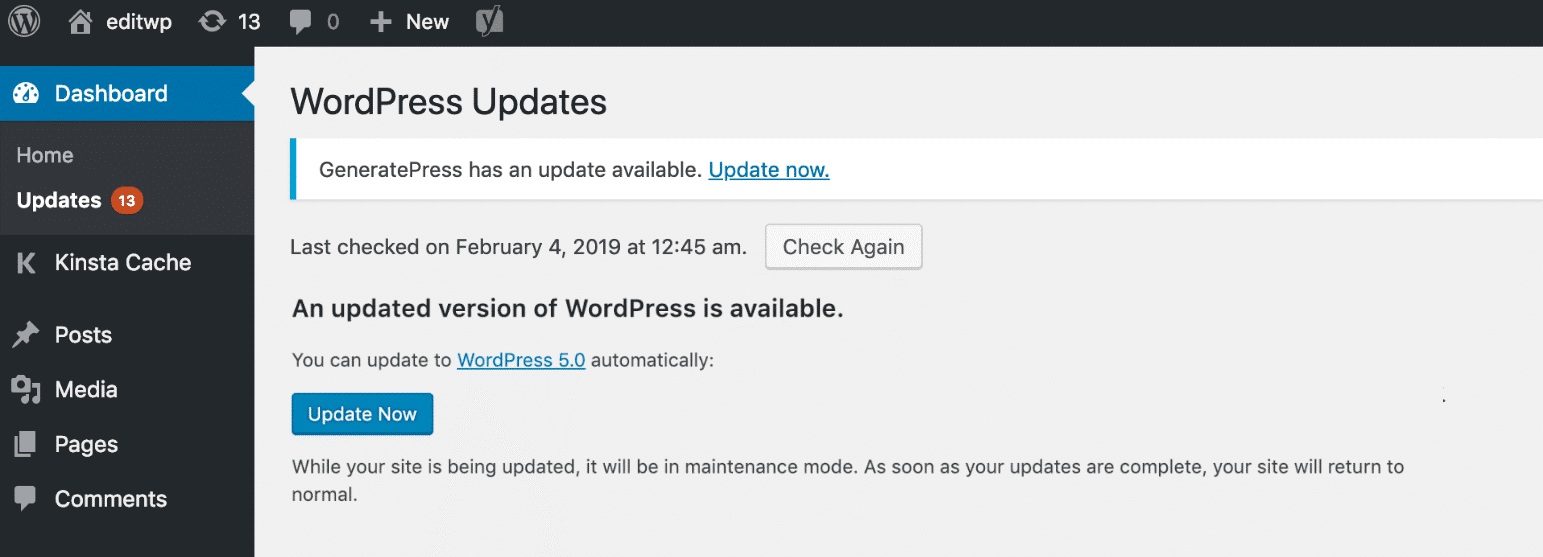
Vulnerabilities in plugins are major known points of entry for hackers to websites.
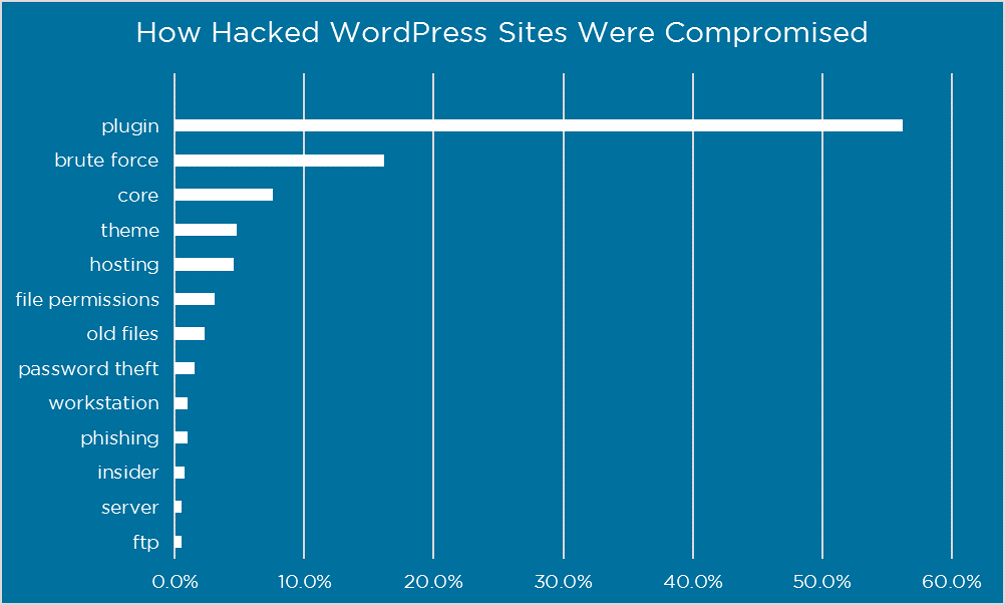
It’s also recommended to install trusted plugins. These are mainly in the “featured” and “popular” categories in the WordPress repository. Alternatively, download from the developer’s website directly. Avoid at all costs nulled plugins and themes: refers to premium WordPress plugins or themes that have been hacked or contain modified code designed to cause harm or collect information. These are obtained from a third-party website (not the original author or creator) and sometimes are made to work without a license key.
To be on the safe side, you can use a tool like VirusTotal to scan a plugin or theme’s files to see if it detects any type of malware or use WPScan to check on vulnerabilities affecting the WordPress core, plugins and themes.
To update WordPress core, you can click into “Updates” in your WordPress dashboard and click on the “Update Now” button. On the same page, you can also choose to update installed plugins and themes by selecting the appropriately.
Lock Down WordPress Admin
Locking down your WordPress admin area and login is a good way to beef up your security. Two great ways to do this is first by changing your default wp-admin login URL and also limiting login attempts. By default, your WordPress site’s login URL is domain.com/wp-admin. One of the problems with this is that all of the bots, hackers, and scripts out there also know this.
You can use plugins to change your WordPress login URL. Most common could be WPS Hide Login or the premium Perfmatters: each has a simple input field for changing the URL. But remember, pick a unique path that a script or bot might try to attempt to scan.
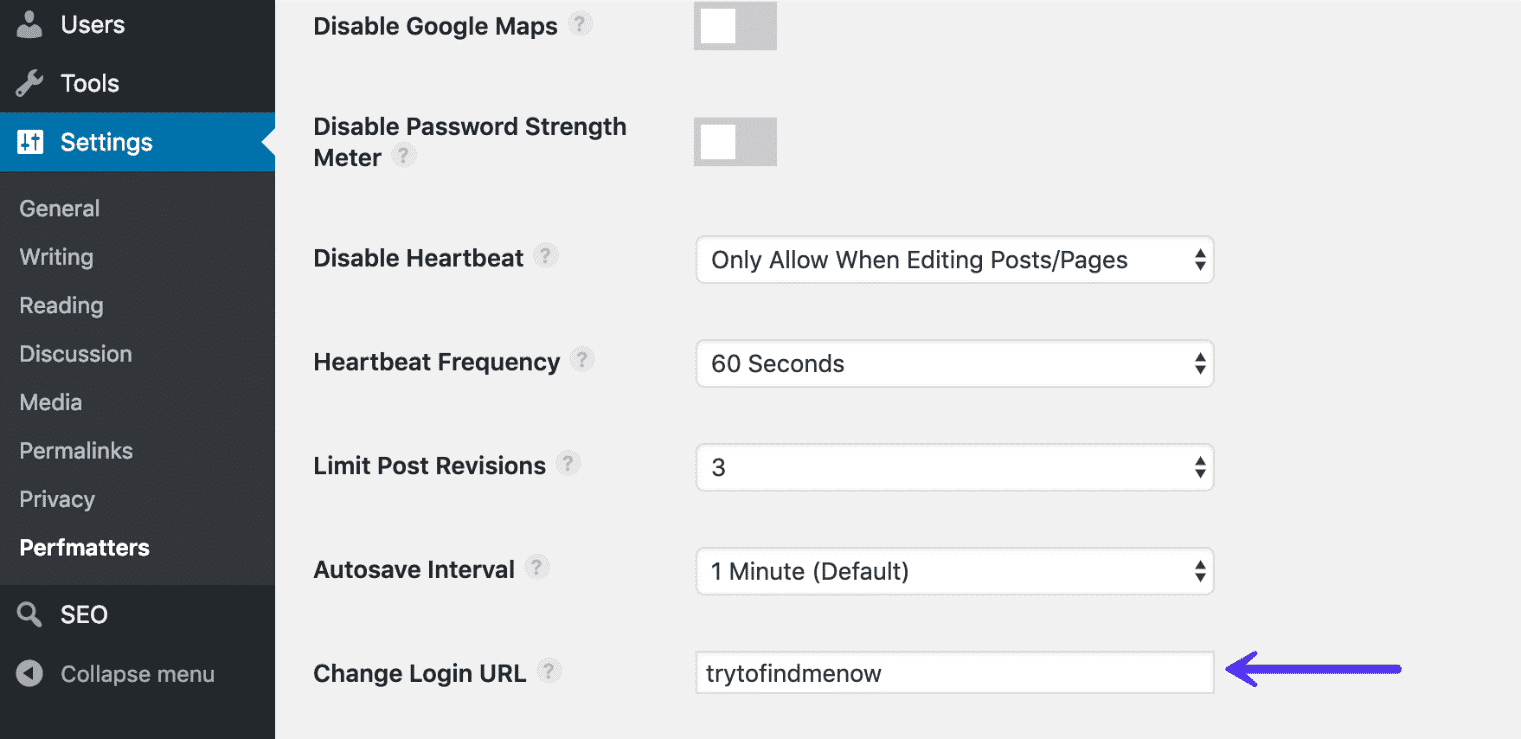
Other solutions to lock down WordPress include limiting the number of login attempts. Cerber Limit Login Attempts can help you achieve that by easily setting up lockout durations, login attempts, and IP whitelists and blacklists.
Locking down a URL path ensures that only your IP address s able to access the WordPress admin login URL to your website. However, this should not be used on ecommerce or membership websites as they also rely on accessing your website’s backend.
Two-Factor Authentication
Two-factor authentication involves a two-step process in which you need not only your password to login but a second method. It is generally a text (SMS), phone call, or time-based one-time password (TOTP). In most cases, this is 100% effective in preventing brute force attacks to your WordPress site.
Two-factor authentication can be implemented on your hosting account and your dashboard (WP). If someone gets access to either of these areas, they could change your password, delete your website, change DNS server records, redirect emails, and much more.
Plugins you can use to protect the WordPress installation include:
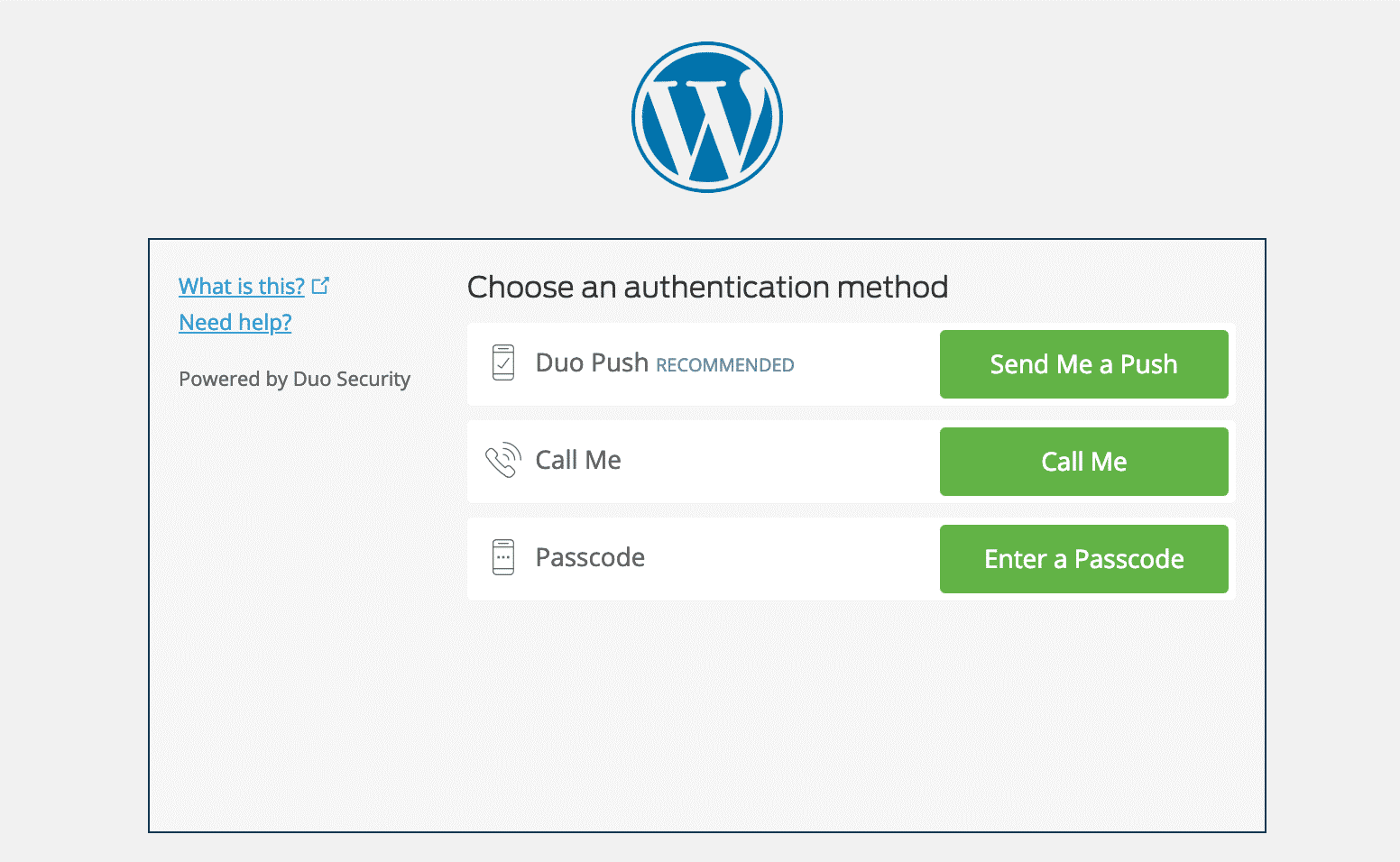
After installing and configuring one of the above plugins, you will typically have an additional field on your WordPress login page to enter your security code. Or, with the Duo plugin, you first log in with your credentials and are then required to choose an authentication method, such as Duo Push, call, or passcode.
This method can easily be combined with changing your default login URL, meaning not only is your WordPress login URL something only you know, but it now requires extra authentication to get in.
HTTPS for Encrypted Internet Connections - SSL Certificate
HTTPS (Hyper Text Transfer Protocol Secure) is a mechanism that allows your browser or web application to securely connect with a website. More so, if you’re an ecommerce platform, this is a mandatory requirement.
Note: Don’t fall for the misconception that only credit card accepting websites need an SSL certificate.
An SSL certificate helps with:
Security: HTTPS is absolutely vital in maintaining a secure connection between a website and a browser. This way you can better prevent hackers and or a middle man from gaining access to your website.
SEO: According to Google, HTTPS is a ranking factor in any website.
Trust and Credibility: Customers trust the green HTTPS padlock, giving them a piece of mind as they consider their data protected.
Referral Data: HTTPS to HTTP referral data is blocked in Google Analytics.
Chrome Warnings: Chrome 68 and above marks all non-HTTPS sites as “Not Secure”.
Performance: Because of a protocol called HTTP/2, a lot of times, those running properly optimized sites over HTTPS can even see speed improvements. HTTP/2 requires HTTPS because of browser support. The improvement in performance is due to a variety of reasons such as HTTP/2 being able to support better multiplexing, parallelism, HPACK compression with Huffman encoding, the ALPN extension, and server push.
To enforce a secure, encrypted connection between you and the server when logging into and administering your site, add the following line to your wp-config.php file:
define('FORCE_SSL_ADMIN', true);
Hardening wp-config.php
The wp-config.php file is the heart and soul of the WordPress installation: most important file when it comes to security. It contains your database login information and security keys which handle the encryption of information in cookies.
Move wp-config.php: By default, your wp-config.php file resides in the root directory of your WordPress installation (your /public HTML folder). But you can move this to a non-www accessible directory.
To move your wp-config.php file simply copy everything out of it into a different file. Then in your wp-config.php file you can place the following snippet to simply include your other file. Note: the directory path might be different based on your web host and setup. Typically, though it is simply one directory above.
<?php
include('/home/yourname/wp-config.php');
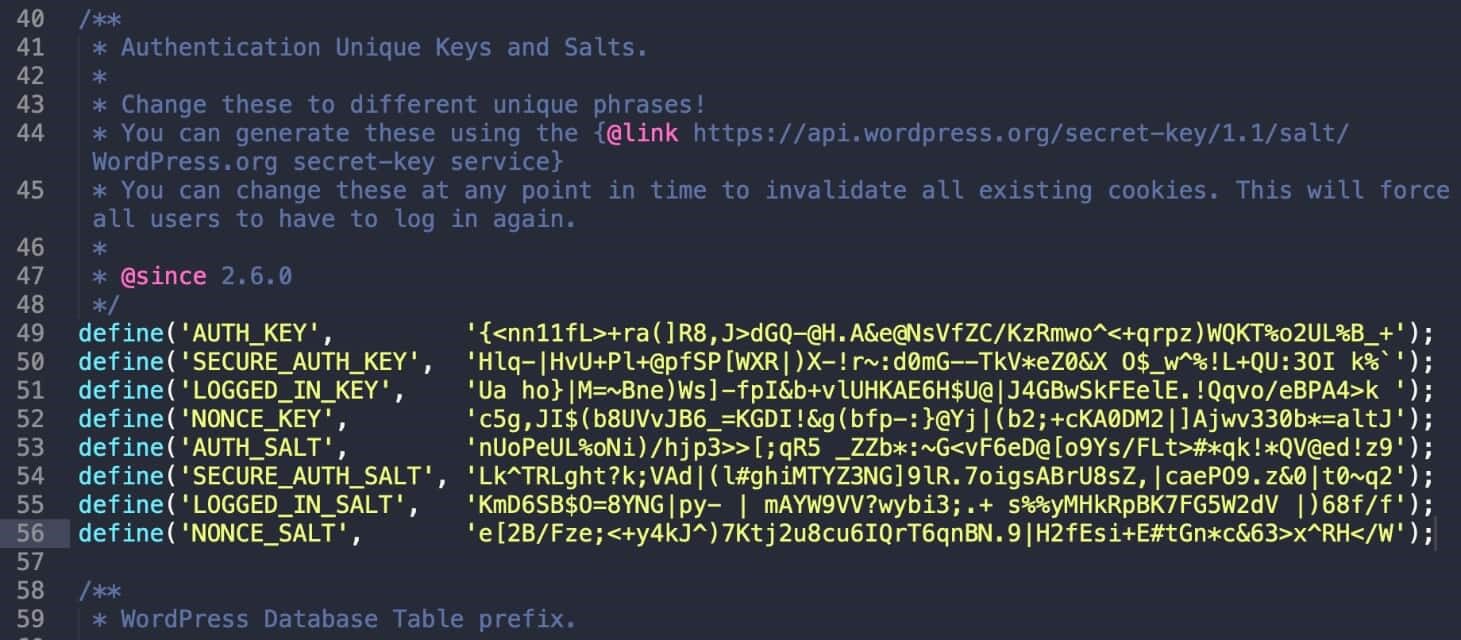
Update WordPress Security Keys: WordPress security keys are a set of random variables that improve encryption of information stored in the user’s cookies. Different keys, generated randomly for you, are in use: AUTH_KEY, SECURE_AUTH_KEY, LOGGED_IN_KEY, and NONCE_KEY. It’s a good idea to change these keys if you’ve gone through multiple migrations or purchased a site from someone else. You can use a free tool from WordPress to generate random keys.
Change Permissions: Typically, files in the root directory of a WordPress site will be set to 644, which means that files are readable and writeable by the owner of the file and readable by users in the group owner of that file and readable by everyone else. According to the WordPress documentation, the permissions on the wp-config.php file should be set to 440 or 400 to prevent other users on the server from reading it. You can easily change this with your FTP client.
Disable XML -RPC
One of the hidden features of XML-RPC is that you can cause the system to multi-call method to execute multiple methods inside a single request. This is very useful as it allows the application to pass multiple commands within one HTTP request.
Hide WordPress Version
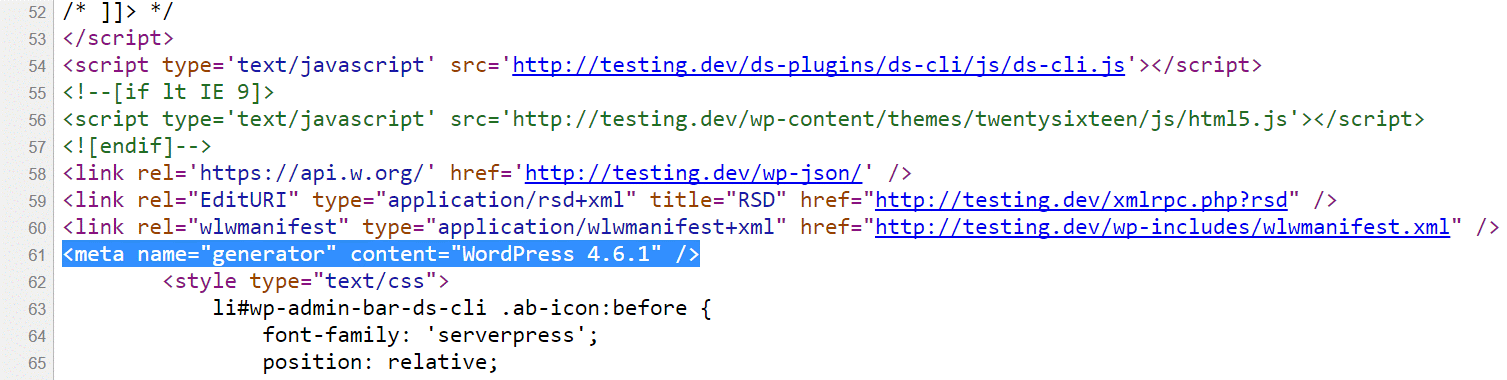
Hiding your WordPress version touches again on the subject of WordPress security by obscurity. By default, the WordPress version shows p in the header of your website’s source code.
Keep the installation up-to-date and all will be well. You can use the following code to remove this. Simply add it to your WordPress theme’s functions.php file.
Caution: Editing the source code of a WordPress theme could break your site if not done correctly. If you are not comfortable doing this, please check with a developer first.
function wp_version_remove_version() {
return '';
}
add_filter('the_generator', 'wp_version_remove_version');
Another place where the WordPress version shows up is in the default readme.html file (as shown below) that is included in every WordPress version. It is located in the root of your installation, domain.com/readme.html. You can safely delete this file via FTP. Though from WordPress 5.0 or higher, the version number is no longer included in the file.
HTTP Security Headers
Security headers are usually configured at the web server level and tell the browser how to behave when handling your site’s content. Most important ones from the several that are available include:
- Content-Security Policy
- X-XSS-Protection
- Strict-Transport-Security
- X-Frame-Options
- Public-Key-Pins
- X-Content-Type
You can check which headers are currently running on your WordPress site by launching Chrome devtools and looking at the header on your site’s initial response.
WordPress Security Plugins
It’s good to have hardware firewalls, active and passive security, by-the-minute uptime checks and scores of other advanced features to prevent attackers from gaining access to your data.
Some notable WordPress security plugins include:
The above plugins have the following features and uses:
Generate and force strong passwords when creating user profiles
- Force passwords to expire and be reset on a regular basis
- User action logging
- Easy updates of WordPress security keys
- Malware Scanning
- Two-factor authentication
- reCAPTCHAs
- WordPress security firewalls
- IP whitelisting
- IP blacklisting
- File changelogs
- Monitor DNS changes
- Block malicious networks
- View WHOIS information on visitors
Another important feature that many security plugins include a checksum utility. This inspects the WordPress installation and looks for modifications on the core files as provided by WordPress.org via the API. Any changes or modifications to these files could indicate a hack. Alternatively, you can also use WP-CLI to run your own checksum.
Database Security
By changing your database name to some more obscure name helps protect your site by making it more difficult for hackers to identify and access your database details.
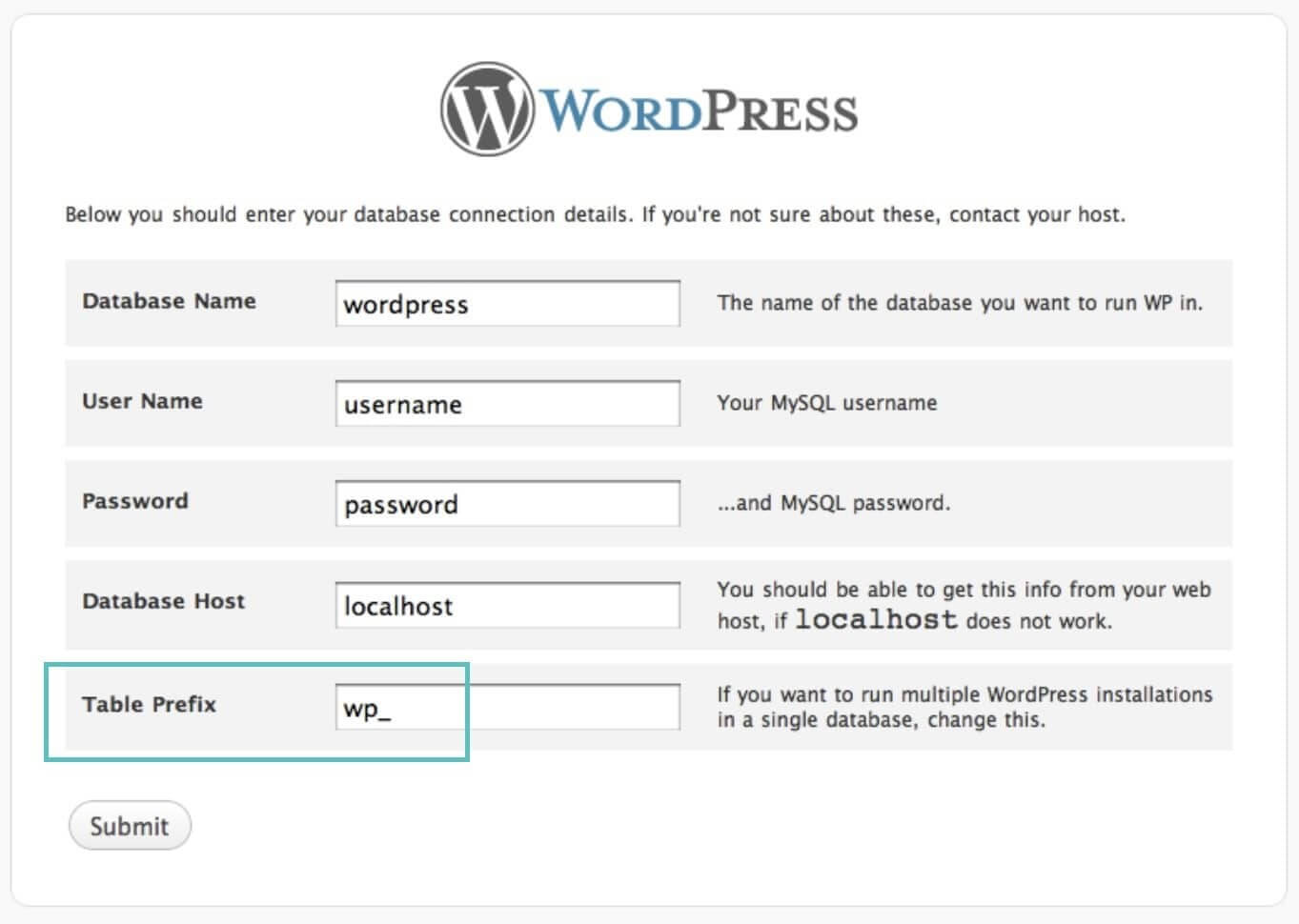
Secondly, change the default database table prefix. By default, WordPress uses wp_. Changing this to something like 78wep_ can be much more secure. When you install WordPress, it asks for a table prefix (as seen below). There are also ways to change the WordPress table prefix on existing installations.
Use Secure Connections for File Transfers
Ensure that your WordPress host it taking precautions such as offering SFTP or SSH. SFTP or Secure File Transfer Protocol (also known as SSH file transfer protocol), is a network protocol used for file transfers.
Also, setup your router correctly. A few simple tips to secure your router would include:
Don’t enable remote management (VPN). Typical users never use this feature and by keeping it off you can keep from exposing your network to the outside world.
- Routers by default use IPs in the range such as 192.168.1.1. Use a different range, such as 10.9.8.7.
- Enable the highest level of encryption on your Wi-Fi.
- IP white-list your Wi-Fi so that only people with the password and certain IP can access it.
- Keep the firmware up to date.
When using a publicly accessible Wi-Fi, take precautions like using a 3rd party VPN to encrypt your Internet traffic and hide your IP address from hackers.
Check File and Server Permissions
If permissions are too loose, someone could easily gain access to your site and wreak havoc. On the other hand, if your permissions are too strict this could break functionality on your site.
File Permissions
- Read permissions are assigned if the user has rights to read the file.
- Write permissions are assigned if the user has rights to write or modify the file.
- Execute permissions are assigned if the user has the rights to run the file and/or execute it as a script.
Directory Permissions
- Read permissions are assigned if the user has the rights to access the contents of the identified folder/directory.
- Write permissions are assigned if the user has the rights to add or delete files that are contained inside the folder/directory.
- Execute permissions are assigned if the user has the rights to access the actual directory and perform functions and commands, including the ability to delete the data within the folder/directory.
typical recommendations for permissions when it comes to file and folder permissions in WordPress. See the WordPress Codex article on changing file permissions for a more in-depth explanation.
- All files should be 644 or 640. Exception: wp-config.php should be 440 or 400 to prevent other users on the server from reading it.
- All directories should be 755 or 750.
- No directories should ever be given 777, even upload directories.
Disable File Editing in WordPress Dashboard
It is important to give users the correct roles and permissions so that they don’t break anything. Because of this, it can be beneficial to simply disable the “Appearance >> Editor” in WordPress. A very bad practice is to give authors or contributors administrator access, unfortunately, it happens all the time.
It is much better to edit the file locally and upload it via FTP. And of course, in best practice, you should be testing things like this on a development site first.
Place the following code in your wp-config.php file to remove the ‘edit_themes’, ‘edit_plugins’ and ‘edit_files’ capabilities of all users.
define('DISALLOW_FILE_EDIT', true);
Prevent Hotlinking
Hotlinking: when you find an image somewhere on the Internet and use the URL of the image directly on your site. This image will be displayed on your website but it will be served from the original location. This is actually theft as it is using the hotlinked site’s bandwidth. May not seem like a big deal, but it could generate a lot of extra costs related to extra bandwidth usage.
Prevent Hotlinking in Apache
To prevent hotlinking in Apache simply add the following code to your .htaccess file.
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yourdomain.com [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ http://dropbox.com/hotlink-placeholder.jpg [NC,R,L]
Prevent Hotlinking in NGINX
To prevent hotlinking in NGINX simply add the following code to your config file.
location ~ .(gif|png|jpe?g)$ {
valid_referers none blocked ~.google. ~.bing. ~.yahoo yourdomain.com *.yourdomain.com;
if ($invalid_referer) {
return 403;
}
}
For blocking hotlinking images from CDN, check the setup of your corresponding.
Take WordPress Backups
Backups are the one thing everyone knows they need but don’t always take. But no matter how secure your site is, it will never be 100% safe. So, you want backups in case the worst happens.
Most managed WordPress hosting providers now provide backups with one-click restoration.
Backups can be done by:
WordPress Backup Services: these charge a low monthly fee and store your backups for you in the cloud. They include:
- VaultPress (from the Automattic team, now part of Jetpack)
- CodeGuard
- BlogVault
WordPress Backup Plugins
WordPress backup plugins allow you to create your backups via FTP or integrate with an external storage source such as Amazon S3, Google Cloud Storage, Google Drive, or Dropbox. We highly recommend going with an incremental solution so it uses fewer resources.
DDoS Protection
DDoS is a type of DOS attack where multiple systems are used to target a single system causing a Denial of Service (DoS) attack.
One of the best recommendations is to use a reputable 3rd party security service like Cloudflare or Sucuri. If you are running a business, it can make sense to invest in their premium plans.
Advanced DDoS protection can be used to mitigate DDoS attacks of all forms and sizes including those that target the UDP and ICMP protocols, as well as SYN/ACK, DNS amplification and Layer 7 attacks.
Summary
There are numerous ways you can harden your WordPress security. Using clever passwords, keeping core and plugins up to date, and choosing a secure managed WordPress host are just a few that will keep your WordPress site up and running safely. For many of you, your WordPress site is your both your business and income, so it’s important to take some time and implement some of the security best practices mentioned above, sooner rather than later.





